In the Hacking World 'Iran is the New China,' Experts Say
| Jose Mario Fuderanan | | Dec 12, 2014 01:29 PM EST |
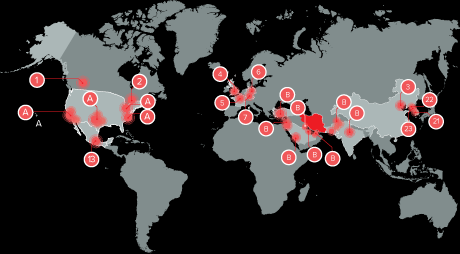
(Photo : Cylance) Iran is now a first-rate cyber power and joins the likes of China and the U.S. as the top countries capable of engaging in cyber attack and espionage, according to some intelligence experts.
Iran is now a first-rate cyber power and joins the likes of China and the U.S. as the top countries capable of engaging in cyber attack and espionage, according to some intelligence experts.
In a recent report, cyber security firm Cylance outlined Iran's protracted and well-coordinated attacks on critical industries, infrastructure and resources in 16 countries, including the United States, Canada, South Korea, India and China.
Like Us on Facebook
Cylance called Iran's cyber offensive "Operation Cleaver" after a string or sequence of characters found several times in the custom-made software of its perpetrators.
"Iran is the new China. Operation Cleaver has, over the past several years, conducted a significant global surveillance and infiltration campaign," Cylance researchers said in the report. "To date it has successfully evaded detection by existing security technologies."
While China had been implicated in several cyber espionage cases in North America before, some experts argue on its true objectives: on whether the purpose was for eventual sabotage if a conflict ever happens, or industrial cyber espionage.
James Clapper, U.S. Director of National Intelligence, said before the Senate Intelligence Committee in January that "China's cyber operations reflect its leadership's priorities of economic growth, domestic political stability, and military preparedness." In plain speak, Clapper is implying that China's hackers may be capable of theft, but they are not terrorists.
With Iran, though, experts are putting out an urgent warning about its openly hostile intentions.
In 2012, after a debilitating cyber attack called Stuxnet at an Iranian nuclear facility widely believed to have been launched by the United States and Israel, Iran's Ayatollah Ali Khameni announced the creation of the Supreme Council of Cyberspace aimed at preventing attacks and carrying out cyber operations against their enemies.
In retaliation for the Stuxnet attack, Iran is believed to have launched sophisticated distributed denial of service (DDoS) assaults on the websites of major U.S. banks in late 2012. It was also blamed for the so-called Shamoon attack on 33,000 computers of Saudi Aramco, the giant petroleum and natural gas company.
In September 2013, a cyber-intrusion into an unclassified U.S. Navy computer network sparked concern that Iranian hackers are becoming more potent and more capable of targeting military data.
In Cylance's extensive report, it says Iran's hackers have compromised computer networks in more than 50 organizations in 16 countries, including airlines and airports, and companies that are involved in technology, utilities, manufacturing, aerospace, chemicals and even health care. Some governments hosting these organizations are targeted as well.
Cylance claims to have been monitoring Operation Cleaver for two years and is composed of teams of hackers and developers recruited from Iranian universities. It said the campaign utilizes publicly available tools and internally developed software and malware.
Operation Cleaver's most resilient weapon is the TinyZBot, a Trojan program they have been using for two years.
But not everyone is overly worried. Though Cylance admits it has only bared a fraction of the systems damaged by Operation Cleaver, other experts say the Iranians are not yet capable of so-called zero-day attacks like Stuxnet , where new classes of vulnerabilities in systems are exploited.
Tony Cole of the cyber security group FireEye told the website Defense One: "Are they the new China? At this point they haven't shown us enough capability to overshadow the continuous attacks of various levels of sophistication from China."
"They might be simply showing the world that they have a capability at this point in the cyber arena or it could be for more nefarious purposes where they plan on creating a cyber attack to have a kinetic and damaging effect in the real world. We hope it's not the latter."
©2015 Chinatopix All rights reserved. Do not reproduce without permission
EDITOR'S PICKS
-

Did the Trump administration just announce plans for a trade war with ‘hostile’ China and Russia?
-

US Senate passes Taiwan travel bill slammed by China
-

As Yan Sihong’s family grieves, here are other Chinese students who went missing abroad. Some have never been found
-

Beijing blasts Western critics who ‘smear China’ with the term sharp power
-

China Envoy Seeks to Defuse Tensions With U.S. as a Trade War Brews
-

Singapore's Deputy PM Provides Bitcoin Vote of Confidence Amid China's Blanket Bans
-

China warns investors over risks in overseas virtual currency trading
-

Chinese government most trustworthy: survey
-

Kashima Antlers On Course For Back-To-Back Titles
MOST POPULAR
LATEST NEWS
Zhou Yongkang: China's Former Security Chief Sentenced to Life in Prison

China's former Chief of the Ministry of Public Security, Zhou Yongkang, has been given a life sentence after he was found guilty of abusing his office, bribery and deliberately ... Full Article
TRENDING STORY

China Pork Prices Expected to Stabilize As The Supplies Recover

Elephone P9000 Smartphone is now on Sale on Amazon India

There's a Big Chance Cliffhangers Won't Still Be Resolved When Grey's Anatomy Season 13 Returns

Supreme Court Ruled on Samsung vs Apple Dispute for Patent Infringement

Microsoft Surface Pro 5 Rumors and Release Date: What is the Latest?